| Topology:
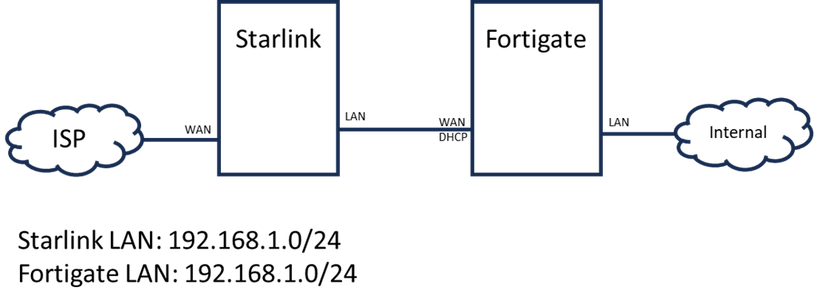
The FortiGate default LAN subnet conflicts with the Starlink router LAN subnet, the FortiGate WAN interface cannot obtain the allocated IP from the Starlink router.
The Starlink router does not provide any option to change its own DHCP Server IP range, ‘192.168. 1.0/24’ is hardcoded.
If the FortiGate LAN subnet cannot be changed, the VDOM can be used to separate the WAN and LAN networks as a workaround.
The config example is shown below:
• Enable multi-VDOM mode:
config system global
set vdom-mode multi-vdom
end
• Create the ‘Internal’ VDOMs:
config vdom
edit Internal
next
end
• Assign interfaces to the VDOMs:
config system interface
edit “wan1”
set vdom “root”
next
edit “port1”
set vdom “Internal”
next
end
• Configure the VDOM link:
config system interface
edit “vlink10”
set vdom “root”
set ip 10.0.0.1 255.255.255.252
set allowaccess ping
set type vdom-link
next
edit “vlink11”
set vdom “Internal”
set ip 10.0.0.2 255.255.255.252
set allowaccess ping
set type vdom-link
next
end
• Configure the default static route to the Internet in ‘Internal’ VDOM:
config vdom
edit Internal
config router static
edit 1
set gateway 10.0.0.1
set device “vlink11”
next
end
• Configure the firewall policies from ‘Internal’ LAN to the Internet:
config vdom
edit Internal
config firewall policy
edit 1
set name “Internet”
set srcintf “port1”
set dstintf “vlink11”
set action accept
set srcaddr “all”
set dstaddr “all”
set schedule “always”
set service “ALL”
set nat enable
next
end
config vdom
edit root
config firewall policy
edit 3
set name “InternaltoInternet”
set srcintf “vlink10”
set dstintf “wan1”
set action accept
set srcaddr “all”
set dstaddr “all”
set schedule “always”
set service “ALL”
set logtraffic all
set nat enable
next
end
Test PC (192.168.1.100) can access to internet in the FortiGate LAN subnet via Starlink router WAN:
Tracing route to dns.google [8.8.8.8]
over a maximum of 30 hops:
1 <1 ms <1 ms <1 ms 192.168.1.99
2 1 ms <1 ms <1 ms 10.0.0.1
3 1 ms <1 ms <1 ms 192.168.1.1
4 7 ms 6 ms 6 ms static-209-87-245-1.storm.ca [209.87.245.1]
5 7 ms 6 ms 6 ms google.ip4.torontointernetxchange.net [206.108.34.6]
6 7 ms 7 ms 7 ms 108.170.250.241
7 7 ms 7 ms 7 ms 216.239.35.233
8 7 ms 6 ms 6 ms dns.google [8.8.8.8]
|


